Sharing is caring!
Customer Relationship Management is critical to the success of every profit-oriented business in today’s times when much emphasis is given to aspects such as data security and best practices. No wonder, CRM giants such as Salesforce spend a lot of resources to ensure that their customers get the best of customizable platforms to make this happen.
In this blog post, we will explore Salesforce security best practices that every business should consider. Following these advanced Salesforce Security best practices will help us get most of the powerful and out-of-the-box Salesforce CRM system. Through it, Salesforce admins can easily leverage all of the platform’s features to safeguard their company and customers’ data.
Before moving ahead, let’s first have a look at two common Salesforce security myths.
Common Salesforce Security Myths
Unauthorized User Access is a Common Threat – Today, malware and unauthorized access to data and computer resources are the top cloud security concerns for businesses of all sizes. They can cause a loss of confidentiality, integrity, and availability of IT resources.
However, security is not too much of a concern when it comes to user access in the context of Salesforce.
- Salesforce offers a robust platform and it can be leveraged to provide different types of solutions across all the bases.
- Salesforce Admins can adopt security measures to prevent malicious users from accessing sensitive Salesforce data.
Employees are NOT a primary threat to data security – The single biggest cyber threat to any organization is its own employees. Inadequate logging and monitoring by employees such as not deactivated properly logging in can significantly affect the level of security. As an administrator, it’s important to keep track of what your team can access and how they impact the data security of the Org.
Salesforce Security Best Practices
Data Sharing
Sharing rules aren’t much related to Salesforce security. However, who has access to which data on the Salesforce platform is very important for the security of each instance’s data.
There is no denying the fact that hierarchical structure has been the source of a great deal of trouble and inefficiency. In terms of data sharing, it is important how data gets shared in the role hierarchy for most administrators, including how users can access a record or set of records because of where they sit in the hierarchical structure.
Another important thing to consider is owner sharing. It is often difficult to identify records that have been shared manually in the backend of Salesforce. Administrators can leverage the Developer Console to identify records that are shared manually.
Implicit Sharing
Salesforce provides implicit sharing model between accounts and child records (opportunities, cases, and contacts) and for various groups of portal users for Salesforce Admins.
The sharing capabilities of the Lightning Platform include a wide variety of features that administrators can use to explicitly grant access to data. Implicit Sharing is when a user gains access to a child record and also gains read-only access to the parent. It is also important to note that changing user roles or role positions in the hierarchy can change access to the child records a user has.
For example, if users have access to child records (as contacts) in the context of opportunities, cases and contacts, and accounts, it means that they have read-only access to the parent account. Conversely, if users have access to an account, it means that they have access to child records (the level of access depends on the role, permission set, etc.).
To Configure child objects that are controlled by parent objects, we need to check the organization-wide Sharing Defaults for Opportunities, Cases, and Contacts from the Sharing Settings.
Lightning Experience: Click on the gear icon>>Setup>>Security>>Sharing Settings.
Set Contact sharing to ‘Controlled by Parent,’ so that sharing access to Contacts is controlled by access to the related Account record.
External Sharing
Salesforce also provides separate External Sharing Org Wide Defaults (OWD) to set a different default access level for external users. Before setting the external organization-wide defaults, make sure the feature is enabled in Salesforce. (Refer to the screenshot below):

After activation, the administrator can enable a second OWD set for external users. It is important to note that a user’s external OWD cannot have greater access than their internal OWD.
Session Settings: Identity Verification
One of the effective ways Admins can enhance the security of their Salesforce instance is by leveraging session settings. Admins can protect the most sensitive parts of Salesforce by enabling the “Raise session to high assurance” option for certain items. This feature can be activated on a lot of things including, Reports and Dashboards, Manage Connected Apps, and more.
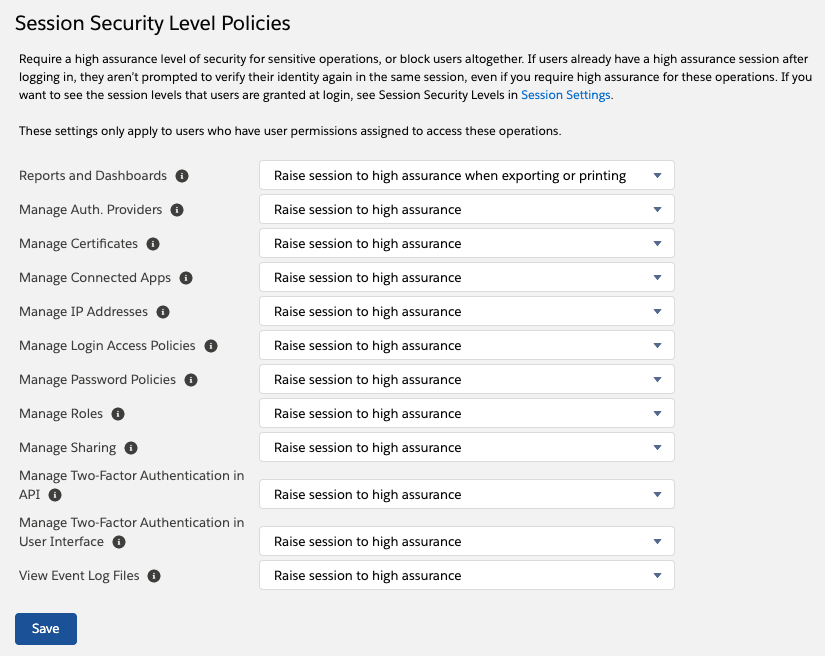
For example, it is recommended to “raise session to high assurance” in Reports and Dashboards while users export or print from reports and dashboards. This means that when a report is printed or downloaded, a user is asked to authenticate.
Session Settings: Session Timeout
In Salesforce, an administrator can configure session settings to log out when the user is in Salesforce and hasn’t been active for a certain period of time. Configuring and Controlling Session Settings on a user profile basis are ideal to set the session timeout duration after two hours.
Here are the steps to configure Session Timeout:
- Go to Setup and search for Session Settings.
- Set Session Timeout for 2 hours.
- Do not disable the session warning popup (do not select).
- Select: Force logout on session timeout.
- Select: Lock sessions to the domain in which they w

Creating Admins with Permission Sets
Profiles in Salesforce is a collection of settings and permissions that allow administrators access to make organizational changes. Admins can create three Permission Sets and each of these Permission Sets can be implemented individually. The permission set group contains the combined permissions of all three permission sets. The three permission sets are User Admin, Record Admin, and Metadata Admin.
User Admin
The user admins in Salesforce is one who has the responsibilities to administer different portions of the org. They perform user management tasks and can assign and deactivate profiles. For example, HR staff must be able to create new users when people are hired and deactivate users when people are fired.
Record Admin
A Record Admin in Salesforce must be able to do things to records in Salesforce but may not allow changes to settings that can affect the Org.
Metadata Admin
The metadata admin can modify, edit, or change in the Setup area of Salesforce and influence Salesforce metadata.
Conclusion
Implementing these above-mentioned best security practices may effectively reduce the risk of data breaches and protect sensitive data from malicious and accidental thefts.
It is important for any data-driven organizations that information should be shared among the users without violating the security concerns. This can be successfully achieved by Roles, Profiles, Permission sets, Organization-wide sharing defaults and sharing rules.
If you are looking to discover more about Salesforce Security Best Practices for Salesforce data, contact Cloud Analogy’s team of certified Salesforce experts now!

Akshay Dhiman
Chief Technical Officer
Akshay Dhiman, the CTO of Cloud Analogy, has been a standout and successful Salesforce Platform Developer for years. He has a rich experience in Salesforce Integration, JavaScript, APEX, VisualForce, Force.com Sites, Batch Processing, Lightning, PHP, C++, Java, NodeJs, ReactJs, Angular 8, GraphQL, React Native, Web Technology, and jQuery.Hire the best Salesforce Development Company. Choose certified Salesforce Developers from Cloud Analogy now.










